You’re accessing archived content
This is archived content from the UIT website. Information may be outdated, and links may no longer function. Please contact stratcomm@it.utah.edu if you have any questions about archived content.
Note: Network News is a semi-regular feature that highlights events in UIT's Network Services group.
Network News: Cisco Tetration promises deep data center insights
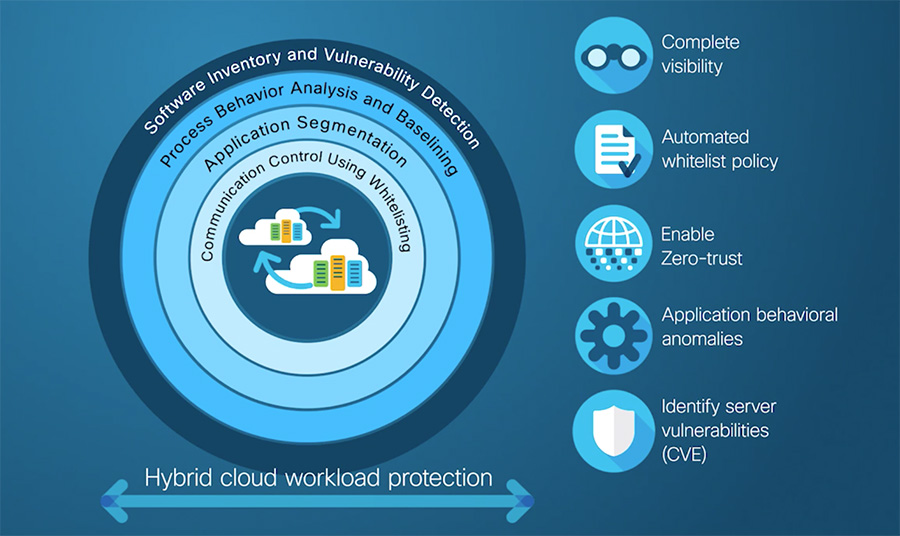
Screen capture from the short video, Tetration Hybrid Cloud Workload Protection Short Overview, courtesy of Cisco Systems. Inc.
UIT is in the process of adding a powerful new analytics platform, Cisco Tetration, as part of a two-phase strategy to convert the University of Utah's enterprise-wide data center services to an application-centric infrastructure (ACI) environment.
Tetration is an automated tool that uses machine learning and behavior analysis to collect telemetry data from Cisco and non-Cisco devices on the network — constantly crunching numbers behind the scenes.
"It's like a big DVR of everything that's happening on the network," said Network Manager Ray Carsey. "It doesn't record content, rather, it keeps track of all of the different traffic flows in a data center."
Sensors allow Tetration to monitor workloads running on hardware, virtual machines (VMs), or in a container, either on-premises or in the cloud.
"Tetration will give the university better insights into its enterprise-wide data center operations," said UIT Project Manager Kevin Buchan. "It collects a massive amount of operational information in real time."
This promises to deliver accurate and timely mapping of communication paths between devices.
"From the information it gathers, we can start analyzing how applications talk to other applications, if there is latency between devices, and then build associated security groups and policies," said Tim Urban, principal engineer in UIT's Network & Core. "Information is also fed back to application owners, which helps them see if traffic is being blocked that shouldn't be blocked and vice-versa."
A key piece to developing security rules with Tetration, Urban said, is application dependency mapping (ADM).
"Usually, in an enterprise organization, one application doesn't live by itself, it has to rely on a lot of different applications — perhaps a web server needs to talk to a database. That ADM run will start mapping that all out and diagram all the communication for us visually in a way that we can put that into policy," he said.
Another advantage of the Tetration platform is tied into the university's disaster recovery (DR) efforts. UIT is undertaking a project around architecting and building a DR presence at the Tonaquint Data Center (TDC) that focuses on payroll for campus. The TDC already houses the University of Utah Health DR site. Urban said Tetration agents have been installed at the TDC, and UIT is starting to analyze the traffic.
Additional aspects of the tool include forensics and the ability to auto-generate "allow list" policies based on application dependency (what's talking to what). Include listing, in this context, is the practice of giving only administrator-approved programs, and IP and email addresses, permission to communicate to a system. Whatever's not on the list is blocked. According to Cisco, Tetration is capable of enforcing tens of millions of whitelist policies across thousands of applications in a hybrid cloud data center.
UIT's Project Management Office (PMO) and Network & Core teams, working with Cisco Professional Services, are on track to install 1,000 Tetration licenses prior to September 2019.

IoT device on your wish list? Connect it to ULink!
Getting an IoT device this holiday?
1. Congrats on making the "nice" list!
2. When it's back on campus, make sure you connect it to ULink.
ULink is the U's newest wireless network, and it's exclusively dedicated to IoT devices like gaming consoles (e.g. Xbox, PlayStation, and Wii), and other entertainment devices (e.g. Apple TV, Roku, and TiVo). It was introduced in campus housing during an extended pilot trial in the fall of 2017, and released campus-wide this past August.
Why a new network? Diverting device-based traffic frees up space on other campus Wi-Fi networks, and that improves network performance for your neighbors. It is, after all, the season of giving. ULink is also more secure than UGuest, and a device-dedicated network discourages the installation of personal wireless routers (rogue access points), which deteriorate the campus network, and in some cases, make Wi-Fi entirely unusable.
To connect to ULink
- Follow these instructions to find your IoT device's MAC address
- Register the device via https://onboard.utah.edu/
- Agree to the Terms & Conditions
- Select Students, Faculty, Staff
- Select Other Devices
- Enter your uNID and password
- Select personal or managed device
- Enter your wireless MAC address
- A password will be generated, and you should receive a confirmation email
- Visit this knowledge article for help configuring common IoT devices
Thanks in advance from everyone on the Network team, and happy holidays.
Node 4
Our monthly newsletter includes news from UIT and other campus/ University of Utah Health IT organizations, features about UIT employees, IT governance news, and various announcements and updates.
