You’re accessing archived content
This is archived content from the UIT website. Information may be outdated, and links may no longer function. Please contact stratcomm@it.utah.edu if you have any questions about archived content.
The U is implementing privileged access management. Here’s why.
Recently, you may have heard a lot about the Information Security Office’s (ISO) push for “PAM” or a university-wide “PAM” solution. If you don’t really understand what PAM is, why you’re hearing about it so much, or why it might be impacting your plans and processes, I hope to provide a clearer vision of privileged access management and why it’s so important.
I’d also like to help everyone understand why the University of Utah/University of Utah Health and our users need to change the way we perform routine administrative and/or privileged work and connect to university resources, such as servers.
What is PAM?
PAM is an acronym for privileged access management. PAM initiatives are efforts to control the use of privileged credentials in our computing environments.
Users with access to privileged accounts can do things that are outside of the scope of what a “normal user” would do any given day. Privileged accounts might have high levels of access, or the ability to change configuration settings, restart services, shut down a computer, etc. They also might be more powerful, and therefore more dangerous, in that they’re shared across multiple machines or multiple users. Some examples: administrative (domain or local) and root accounts, service accounts, and accounts that control the use/configuration of databases, web services, etc.
Why do we need PAM?
The emphasis on, and urgent need for, a PAM solution is based on fundamental changes in the global information technology and cyberattack landscape.
The tools employed by threat actors have evolved to allow less-skilled attackers to be more successful, much more efficient, and much faster. Criminals are constantly scanning, phishing, and engaging in social engineering. The level of sophistication, automation, and activity from threat groups has never been higher, and higher education and health care are among their most popular and lucrative targets.
Criminals also have been taking advantage of current events, like the COVID-19 pandemic, to carry out cyberattacks on individuals and organizations. Consider, for example, the shift in the way we work, collaborate, and access data. Many of us now work from home, in potentially unsafe or less safe computing environments. When our digital habits and environments change, particularly without the additional security measures that the university provides, that makes it easier for criminals to carry out an attack.
Additionally, the number of ransomware attacks has increased exponentially. The success of the ransomware industry has assured that more malware will enter the market, including attacks by state-sponsored actors.
Due to these threats, the 2021 Verizon Data Breach Investigation Report (DBIR) recommended that organizations prioritize Center for Information Security (CIS) Controls 5 and 6, which focus on account and access control management.
So, the university must be more proactive and careful, and we must find new ways to slow attackers down, giving our defenders more time to see them and respond. Perhaps the most effective way is by denying them the use of IT privileges.
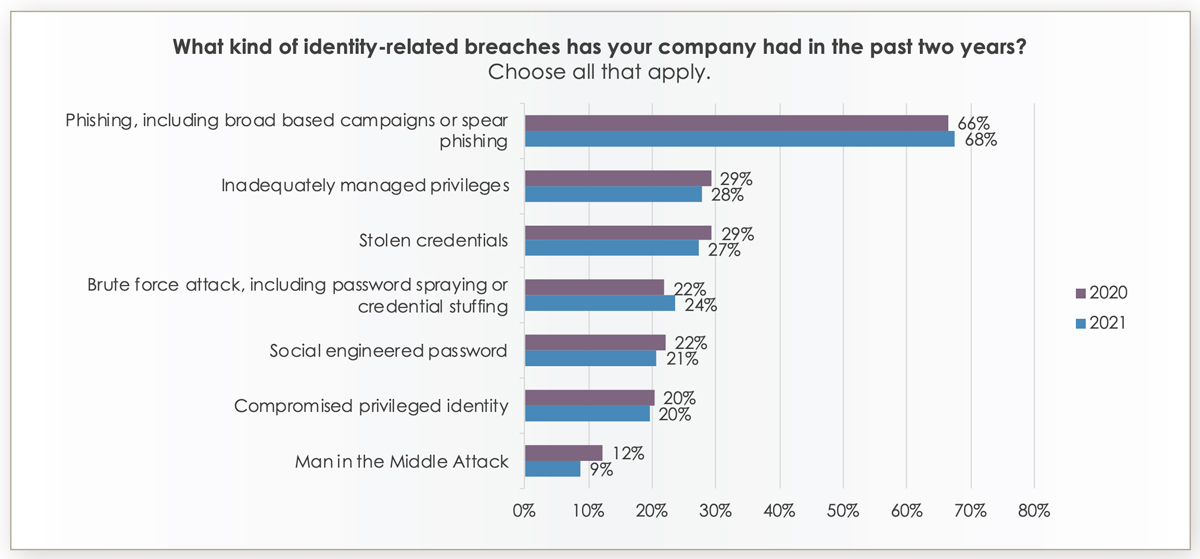
According to a 2021 Identity Defined Security Alliance report, survey respondents indicated that inadequately managed privileges accounted for 28% of identity breaches in the past two years.
What’s the goal?
The goal of the U’s PAM program is to control the availability and use of IT privileges. This includes all privileged users at the University of Utah and University of Utah Health, including affiliates, contractors, and vendors (part of the solution will address external users specifically). I’ll walk you through the phases and how it will work, but the short version is that all privileged access will be required to comply with the PAM program and use the PAM solution.
The U is working toward a “zero-trust” approach in which everyone must be verified for access. For example, we won’t allow access based solely on location (e.g., a campus network or IP address); we will require authentication no matter where the request originates. We’ll work toward “zero standing privileges,” where privileged accounts are not readily available when they’re not in use, and where privilege is assigned, or enabled, on a “just-in-time” basis. Everything we do will be based on the principle of “least privilege,” where we avoid the use of broad permissions or accounts that are given more access than they need.
Not all use cases will support the goals we’re trying to accomplish, and we’ll work to ensure an orderly transition in which services are impacted as little as possible. Most of us don’t like a lot of change in our daily lives and the way we do our work, and we understand that. The world around us, however, is changing, and some of the practices that have worked for us in the past do not work for us now and will not work for us in the future. The way we previously used, controlled, and maintained accounts is one of those things. The (mis)use of stolen credentials/accounts plays a part in about 61 percent of successful breaches, and we must improve our IT security practices.
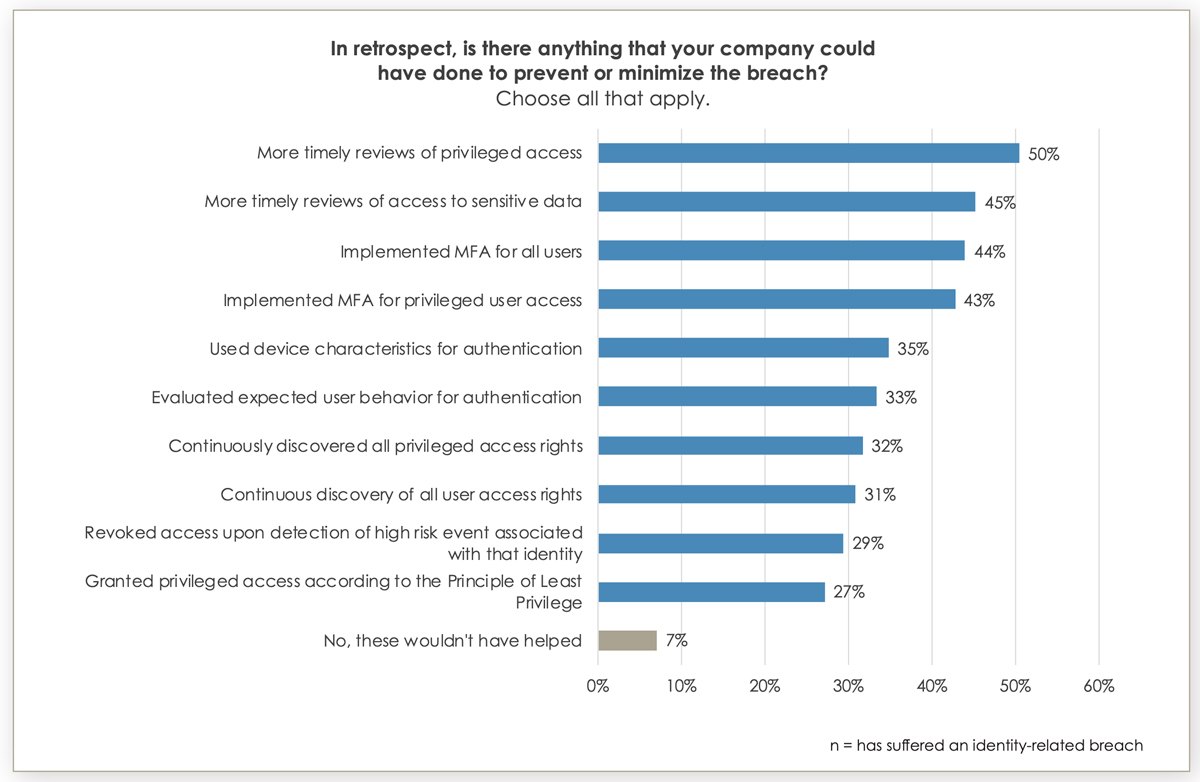
According to a 2021 Identity Defined Security Alliance report, survey respondents indicated more timely reviews of privleged access as the top IT security measure they could have taken to prevent or minimize a breach.
What's the solution?
In a broad sense, the solution is better information security practices and processes around our use of IT resources. However, the specific technical solution we’ve selected to help us reach this goal is a pair of products made by BeyondTrust.
The university has licensed Password Safe (PWS) and Privileged Remote Access (PRA), aka Secure Remote Access (you’ll hear ISO use both terms). PWS will primarily serve internal users (those with uNIDs); PRA will primarily serve external users (people or organizations without a uNID). There will be exceptions — use cases for which PRA might be a better solution, even for an internal user/group, and use cases for which the best answer is to make that person/entity an affiliate to facilitate the use of PWS rather than PRA.
BeyondTrust's Password Safe is one solution the university has licensed. (Image from BeyondTrust)
What’s the plan?
Implementing a PAM solution is a complex task that requires partnership and assistance across the organization. Our implementation includes three phases: deploy and discover; access, test, and refine; and defend and operationalize.
Deploy and discover: This phase is underway. We’ve built, configured, and tested the BeyondTrust solutions. With the help of the Chief Technology Officer organization, we have also identified about 4,000 servers and started to deploy accounts that will restrict access to those resources.
Access, test, and refine: In this phase, we will ask system owners to use BeyondTrust to access their resources; document any shortcomings or inefficiencies; help us identify and remove unnecessary accounts; and pare down credentials and permissions to meet the rule of least privilege. The PAM project team will work with teams to answer questions, help to resolve issues, and facilitate the initiative.
Defend and operationalize: In this phase, we will start to better protect our resources; build and improve integrations with other systems and processes; and monitor and control user activity and sessions. We can also review user activity and analyze it to improve operations or determine the root cause of a security incident.
Cybersecurity is everyone’s job
The university and its resources — whether virtual, physical, or human — are under attack every day. Poor control of accounts, especially privileged accounts, can allow attackers to move from resource to resource quickly and easily, often without alerting or warning our defenders because the attack looks like normal movement.
By implementing stronger controls on privilege, and on all accounts for those resources, we can make the attackers work much harder to move around, laterally (to other resources) and vertically (to move from the credentials they have to better credentials).
In the IT security world, we frequently say that cybersecurity is everyone’s job, and we sincerely appreciate all that you do to help us stay safe online. The good news is that the PAM program will make our jobs a little easier from now on.
In future Node 4 articles, we’ll dig a little deeper into privileged access management, why we need it, the BeyondTrust products, and more. If you want more details, have an idea to contribute, or want to discuss any of this, please contact me at chris.stucker@utah.edu.
Node 4
Our monthly newsletter includes news from UIT and other campus/ University of Utah Health IT organizations, features about UIT employees, IT governance news, and various announcements and updates.
