You’re accessing archived content
This is archived content from the UIT website. Information may be outdated, and links may no longer function. Please contact stratcomm@it.utah.edu if you have any questions about archived content.
Digital security tip: Prepare for seasonal cyberattacks

Chris Stucker, associate director, Identity & Access Management
Another year is coming to a close. As we prepare for sugar plums, roasted chestnuts, and other holiday traditions, criminals are thinking about the ways they can capitalize on current events and issues this season. By thinking ahead and staying alert, however, we can better prepare for potential phishing schemes, social engineering, and other cyberattacks.
As always, you can anticipate some obvious messages during the holiday season. For example, you may receive a message saying that an order has a problem or that your credit card is about to be charged $52,000, and you can fix it if you “click here.”
Fraudulent shipping and tracking emails and notifications are also popular phishing schemes. If you receive a message that says something like “click here now or your package will not be delivered,” please do not open the link. If you did order something, go to the website where you purchased the item — manually, by typing the URL in your browser or using your own bookmark/shortcut — and track it there. Attackers use this tactic because it works well. If you have even the tiniest doubt, don’t open the link. Verify it manually and report the message as a phishing attempt to phishing-report@us-cert.gov.
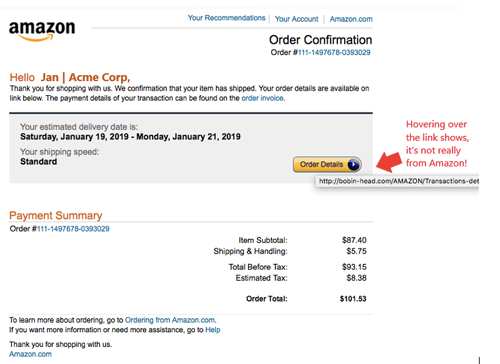
Fraudulent shipping and tracking emails and notifications are popular phishing schemes.
This year, you can expect criminals to leverage the ongoing pandemic, social topics like climate change, and supply chain issues in their attacks. For example, you might receive an email that says the year’s hottest toy, which has been difficult to find, is only a click away — and at a reasonable price.
Attackers also may use QR codes, which are more prevalent than ever. We often talk about the idea that when you open a link you are saying, “I trust you — take me where you want,” but we don’t talk about the fact that a QR code is essentially a link, and you should treat it with the same caution.
Cybercriminals will use all these tactics and more to entice you to open a link or attachment, download a file, provide personal information, or visit a website. Some of their ploys are well-crafted, so knowing what to expect when we receive these messages should help us to remember that criminals are actively trying to take advantage of us and current events.
Remember what you’ve been taught:
- If something sounds too good to be true, it probably is.
- Also, if it sounds too bad to be true, it probably is.
- If an email, call, or message seems unusual or scares you, making you think you need to act, it’s probably a scam.
If you receive a phishing attempt through a university email account, forward the email as an attachment to phish@utah.edu and U Police at uupd-tips@utah.edu. If you’re not sure whether an email is a phishing attempt, send it to phish@utah.edu anyway, and let the ISO analyze it.
All the gifts you’ll be offered through email and text messages? They’re questionable. The Information Security Office’s gift of free email/phishing analysis is solid. It’s like the jelly of the month club — a gift that keeps on giving all year long.
Resources
From the Information Security Office:
- Phishing fundamentals: 3 tips to shore up your defenses
- Why so many phishing attacks succeed
- Common scams — and how to spot them
- Scam safety tips
- IT Knowledge Base article: Phishing
From trusted information security organizations and government entities:
- Keep the Holidays Merry & Bright - Beware of These Sneaky Seasonal Phishing Scams
- What Seasonal Phishing Scams Does Our Team Need to Watch For?
- Watching out for Seasonal Scams
- Threat Intelligence: COVID-19 Proof of Vaccination Scams
- These phishing emails use QR codes to bypass defences and steal Microsoft 365 usernames and passwords
- 12 Examples of Ransomware Attacks
- Must-Know Phishing Statistics: Updated 2021
- The Dirty Dozen represents the worst of the worst tax scams
Node 4
Our monthly newsletter includes news from UIT and other campus/ University of Utah Health IT organizations, features about UIT employees, IT governance news, and various announcements and updates.
