The U’s ISO rolls out new phishing awareness efforts
Earlier this month, IT emailed University of Utah and University of Utah Health employees, asking them to check their passwords right away to ensure they complied with an updated password policy. Some did, using the provided link.
Or so they thought.
The email was a simulated phishing attempt — an exercise by the U’s Information Security Office (ISO) in conjunction with KnowBe4, a well-known cybersecurity and phishing awareness company. Employees received an email from U Human Resources and Chief Information Security Officer Corey Roach about the awareness campaign in late February.
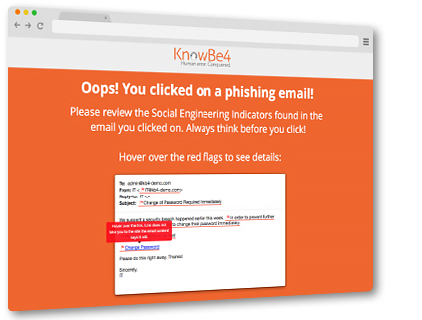
If a user falls for a simulated phishing email, they will be directed to a KnowBe4 webpage, which includes information about the red flags of the fake phish, and enrolled in an IT security awareness course. (Courtesy of KnowBe4)
Employees who opened the link in the email were directed to a KnowBe4 webpage, which included information about the red flags of the simulated phish, and enrolled them in an IT security awareness course. The module covers a range of topics, including the danger of opening links in malicious messages.
The goal of the U’s phishing and cybersecurity awareness efforts is to educate employees (and soon, students) in a safe practice environment about phishing, social engineering, and other online threats so they can better protect themselves and the university against increasingly brazen criminals, said Rudy Matthes, a data security analyst for the ISO’s Governance, Risk & Compliance (GRC) team.
“Criminals are getting better at phishing and social engineering, and U employees and students are falling behind. We need to catch up,” Matthes said. “We need to be more cybersecurity aware, more aware of attackers’ tactics.”
He said the interactive course, which includes slides, videos, and activities, takes about 15 minutes to complete. It covers common attacks and strategies employed by cybercriminals, including phishing and social engineering. Enrolled users will receive an email every week until they complete the training, however, the ISO requests that they complete the course as soon as possible. The module is a fundamental component in the university’s efforts to improve cybersecurity awareness across the organization.
“The module is awesome,” Matthes said. “When I tested it, I thought, ‘I wish my wife, kids, and parents could take this.’ It is good practice.”

The Phish Alert Button will be integrated with all UMail accounts for Outlook clients.
Phish Alert Button
Earlier this month, the ISO also launched KnowBe4’s Phish Alert Button, which makes it easier to report suspicious emails to the ISO’s Security Operations Center (SOC) for review and response.
“We wanted to make it as easy as possible to report a phish. The Phish Alert Button saves a few steps … compared to forwarding an email as an attachment,” Matthes said.
Currently, the button is available only to those who request it. Eventually, however, it will be integrated in all employee and student UMail accounts. The tool works in Outlook Web Access (OWA) and Outlook desktop and mobile clients. The ISO also is exploring the option to add the button to the university’s GCloud accounts.
Users will still be able to forward suspected phishing as an attachment to phish@utah.edu if their email clients (e.g., Apple Mail) do not have the tool, although the Phish Alert Button is the ISO’s preferred way to report suspicious emails.
… Or suspicious emails that might be simulated phishing campaigns.
Trevor Long, associate director for GRC, said simulated phishing campaigns and online security awareness efforts are standard procedures for most large organizations, such as higher education institutions and health care systems.
“University of Utah and University of Utah Health community members should expect them as a regular and routine activity of the U’s cybersecurity program,” Long said, noting that the phishing and IT security awareness effort complies with University of Utah Information Security Policy 4-004, requirements in numerous grants and contracts, and various local, state, federal, international, and industry regulations.
Matthes added that mock phishing exercises are good practice because they’re designed to take you by surprise like a real phish.
He also said simulated phishing campaigns are meant to educate employees, not shame them.
“The university would rather you make mistakes in a safe environment and learn from them than fall for a real phish,” Matthes said. “The U is doing this to help protect you and the university from criminals.”
What is phishing?
A criminal impersonates an organization or person via email to trick you into providing personal and/or other sensitive information. More information.
How do I report phishing?
If you receive a phishing attempt through a university email account, the Information Security Office (ISO) asks that you immediately report it by forwarding the email as an attachment to phish@utah.edu.
For more information on how to report suspicious emails, please visit this IT Knowledge Base article.
What are the U’s phishing and online security awareness efforts?
The U’s Information Security Office has enlisted KnowBe4, a well-known cybersecurity and phishing awareness company, to prepare, protect, and educate our students, faculty, and staff about phishing and other online security issues.
The efforts will consist of simulated phishing emails, brief online awareness learning exercises, and a variety of fliers and handouts. Faculty and staff must participate; students will be required to participate later.
For more information about the awareness efforts, please visit this webpage.
Node 4
Our monthly newsletter includes news from UIT and other campus/ University of Utah Health IT organizations, features about UIT employees, IT governance news, and various announcements and updates.
