U-wide cybersecurity program establishes unit-level tools and reporting

Commissioned by the Office of the President and Board of Regents, with the backing of Chief Information Officer Steve Hess and Chief Information Security Officer Corey Roach, a multiphased cybersecurity initiative led by the Information Security Office (ISO) and UIT Partner Relationships is now underway.

U President Taylor Randall (courtesy of the University of Utah)
“Higher education, and the University of Utah in particular, face an ever-growing cybersecurity threat landscape. All institutions of higher learning are experiencing a steep rise in ransomware attacks, higher premiums for cyber insurance, and the potential loss of contracts should they fail to meet external regulatory requirements,” said Clay Postma, director of UIT Partner Relationships, a new group that reports to Deputy Chief Information Officer Ken Pink. “Even decisions individuals make about their own cybersecurity put the institution at risk. It’s kind of like the old neighborhood fire watch — if your neighbor’s home is on fire and you’re not careful, that puts your home at risk, too.”
The new initiative addresses key findings of an external assessment of the U’s cybersecurity posture that was completed in August 2022. Mitigating the vulnerabilities identified in the assessment, Postma said, will help to ensure a safer and more secure IT environment for students, patients, faculty, staff, and affiliates.
The initiative’s principal goals — implementing a suite of cybersecurity tools at a college/department/organization-level and associated outreach efforts by UIT — also fulfills President Taylor Randall’s commitment to “enhance the campus-wide cybersecurity strategy” as outlined in his Operation Bold Transition recommendations.
“In the short term, these efforts will go a long way to improving the university’s incident response and detection capabilities across the board,” Roach said. “Our hope is that, in the future, a cybersecurity event that previously would have taken weeks or months to remediate will take mere minutes with the appropriate tools in place.”
New cybersecurity initiative: Five strategic goals
- Conduct a third-party assessment of university-wide IT security (complete).
- Increase the likelihood of obtaining cyber insurance by deploying cybersecurity tools.
These implementations, centrally funded through the ISO, must align with:
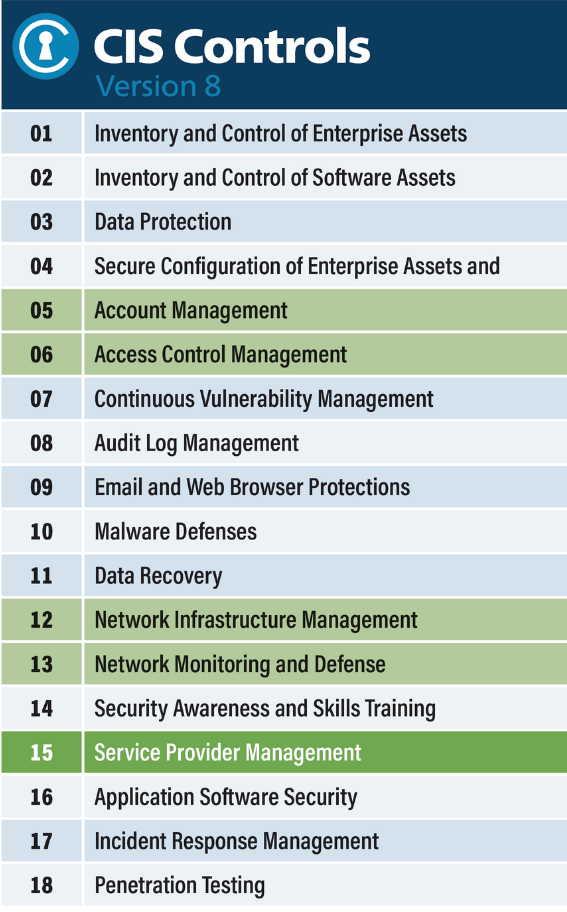 Center for Internet Security (CIS) 18 controls. CIS 18 controls, formerly SANS Critical Security Controls (SANS Top 20), are a series
of recommendations for preventing the most prevalent types of cyberattacks. The CIS
18 controls align with established frameworks and provide a starting point for compliance
with the regulations and standards the university is required to abide, which include
the Health Insurance Portability and Accountability Act (HIPAA), Family Educational Rights and Privacy Act (FERPA), Federal Information Security Modernization Act (FISMA), Centers for Medicare & Medicaid Services (CMS), and Payment Card Industry Data Security Standard (PCI DSS).
Center for Internet Security (CIS) 18 controls. CIS 18 controls, formerly SANS Critical Security Controls (SANS Top 20), are a series
of recommendations for preventing the most prevalent types of cyberattacks. The CIS
18 controls align with established frameworks and provide a starting point for compliance
with the regulations and standards the university is required to abide, which include
the Health Insurance Portability and Accountability Act (HIPAA), Family Educational Rights and Privacy Act (FERPA), Federal Information Security Modernization Act (FISMA), Centers for Medicare & Medicaid Services (CMS), and Payment Card Industry Data Security Standard (PCI DSS).- Utah System of Higher Education IT Resource Security Policy R345.
- Standards established in the U’s Information Security Policy 4-004, which outlines all the university’s IT security rules that help protect the university, its IT systems and resources, and data.
- Implement cybersecurity maturity model certification (CMMC) 2.0 standards, where applicable, that meet federal grant and contract requirements.
- Establish college/department/organization-level IT security reporting responsibilities with the ISO.
- Measure progress toward industry standards (e.g., CIS 18) and the U’s desired security state.
As directed by President Randall, with approval of the President’s Cabinet and the Council of Academic Deans, the initiative is mandatory and applicable to all U of U units.
To date, Postma said UIT Partner Relationships has met with more than a dozen colleges, centers, and administrative units, with more on the schedule. The consultations are designed to help groups implement and document compliance requirements with existing and emerging IT security policies, initiatives, projects, and programs, and understand the consequences for non-compliance. The meetings, Postma said, typically involve planning sessions with local IT support teams to inventory all managed IT systems and devices.
The following cybersecurity tool sets, Postma said, are either in development or fully deployed in the U’s IT environment:
- Network access control (NAC), an IT security control that restricts unauthorized users and devices from accessing a network.
- Protect by default at the network perimeter, a security model that blocks any inbound network traffic not expressly permitted by various policies; at the firewall level, this involves defining permissible ports and protocols, and turning everything else off.
- Duo Mobile, the University of Utah’s two-factor authentication (2FA) service, which is required to log in to certain U digital resources, including UMail, Campus Information Services (CIS), and Canvas.
- Data loss prevention (DLP) software that detects and helps prevent data breaches, exfiltration, or unwanted destruction of sensitive data.
- Privileged access management (PAM) using BeyondTrust, an IT security solution that encompasses endpoint privilege management (EPM), a way to manage administrative privileges on computers, by giving individual users enough access to perform their roles Endpoint detection and response (EDR) using Tanium, a cybersecurity platform that scans the U’s network endpoints for vulnerabilities and compromises, and helps to rapidly contain them.
- Microsoft Defender for Endpoint, an enterprise endpoint security platform designed to identify and block malicious activity directly on devices like workstations and servers.
If a particular security tool cannot be installed because, for example, a device or IT system is running specialized instrumentation or hardware configurations critical to a research project, network segmentation may be required, and a policy exception must be submitted to the ISO. All exceptions, Postma said, will be revisited annually or more often as needed per Policy 4-004.
The ISO will verify that all recommended tool sets are implemented. As part of the verification process, Postma said, the ISO will check against data protection policies. Data encryption will be required for restricted or sensitive university data in adherence to Rule 4-004C: Data Classification and Encryption.
If you have questions about this initiative, please email Postma at clay.postma@utah.edu.
Other resources include a Unified Security Toolset Microsoft Teams channel (access permission required) and weekly online office hours via Teams held each Thursday from 3:00 p.m. to 4:00 p.m.
Node 4
Our monthly newsletter includes news from UIT and other campus/ University of Utah Health IT organizations, features about UIT employees, IT governance news, and various announcements and updates.
